Secure your network,
_
An AI-based Network Detection & Response solution (NDR) to identify cyber intrusions at the earliest stage and disable attackers.
Explore our NDR solution
Download the datasheetMetalearner
The Metalearner is an AI-based technology designed and developed in the Custocy laboratory. The procedures used during an attack can last from a few seconds (a malicious file upload) to several weeks (data exfiltration).
Our innovative approach has been to create a community of IA who inspect the network at different time scales and who regularly consult each other to agree on the severity of a threat. The Metalearner orchestrates all these AI to give the final decision to the cyber analyst by categorising the predictions in the Custocy interface with a threat score.
Our tests on real attacks show that aggregating multiple AI is more accurate and generates 88 times fewer false positives than an approach that only considers a single time scale.
Deployment
Custocy NDR can be deployed without risk, alone or in conjunction with your existing SOC tools. A network expert and a data analyst are dedicated to guide you.
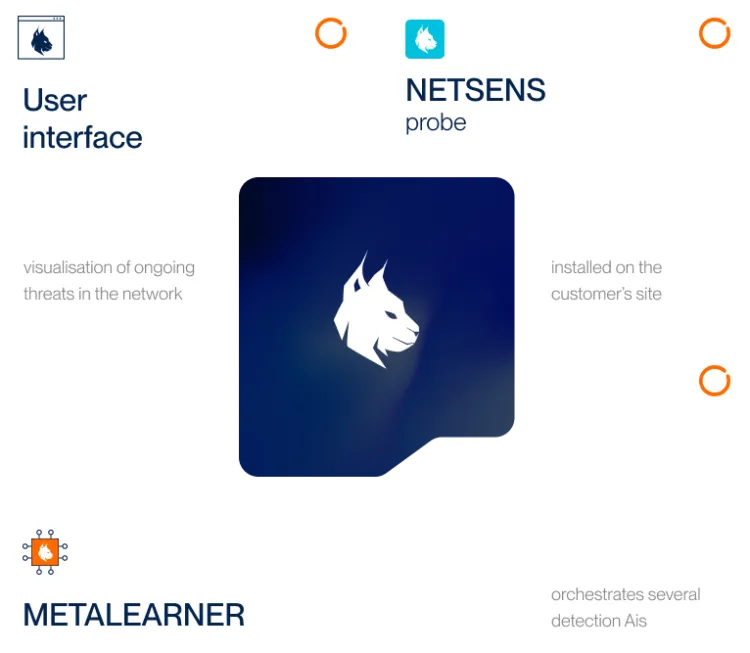
Architecture
Our NETSENS probe is installed on-site, within your infrastructure. It collects and analyses network data on your site. It then connects to the AWS cloud via security access and only sends statistical data or alerts provided by the probe for AI analysis.
Our AI master, the Metalearner, hosted on AWS, receives thousands of events, prioritises them and feeds them back into the Custocy interface with a threat score.
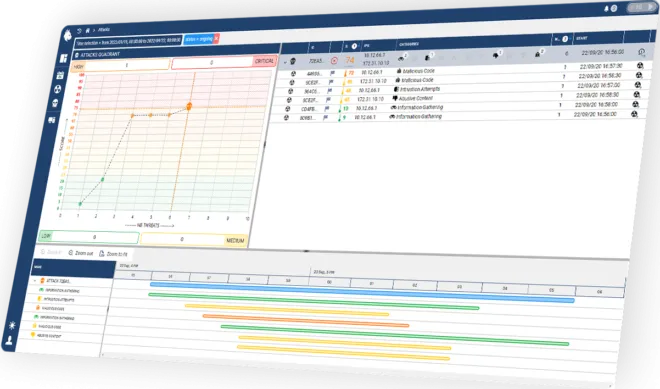
The cyber analyst sees the most important threats appear in real-time. Their priority is colour coded making security management easier.


Proactively reduce your vulnerabilities
Real-time detection by AI
The Custocy NDR leverages the power of its unique collective intelligence technology, which brings together multiple AI working at multiple time scales, to detect threats. Our AI blends advanced behavioural analysis and weak attack signal characterisation to reduce false alarms and detect threats even on encrypted data.
Threat Prioritisation
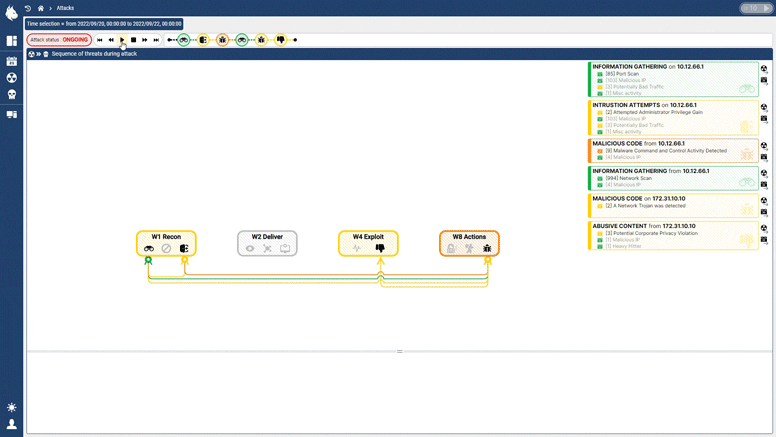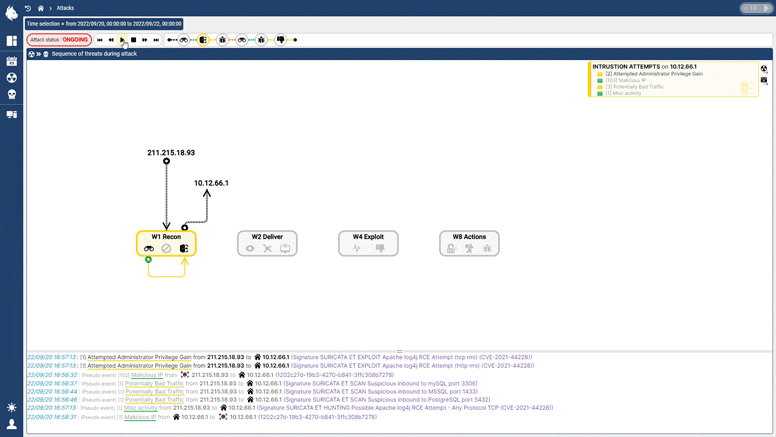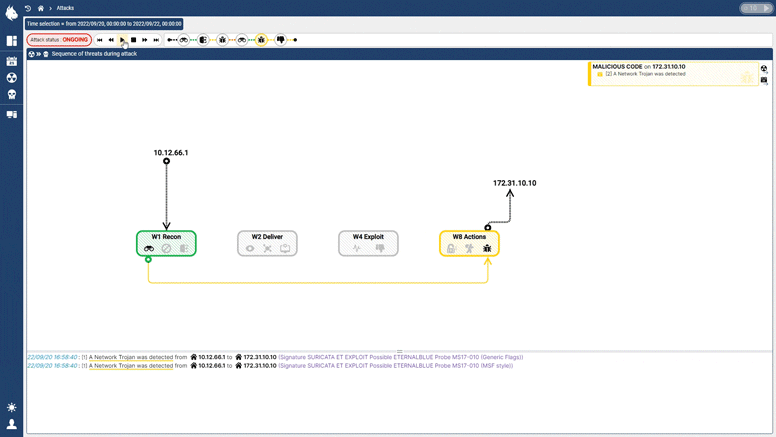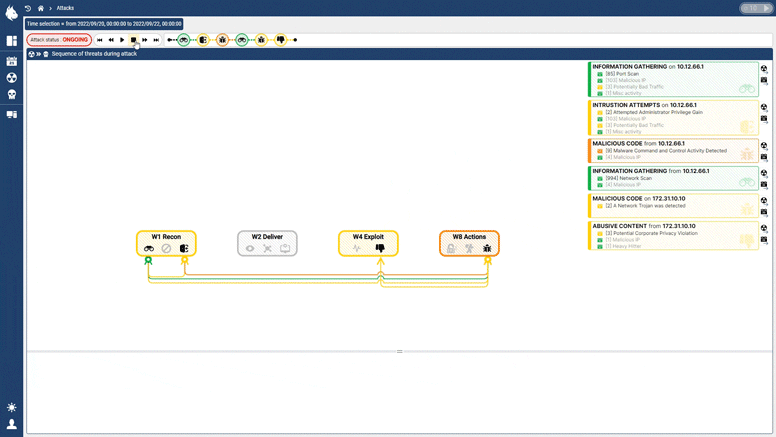
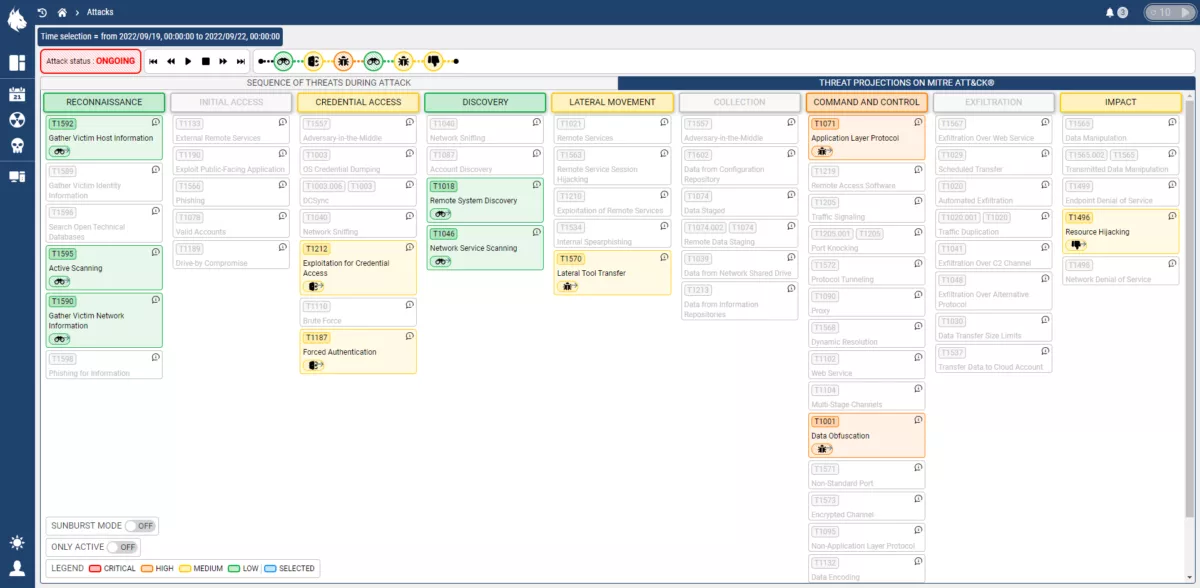
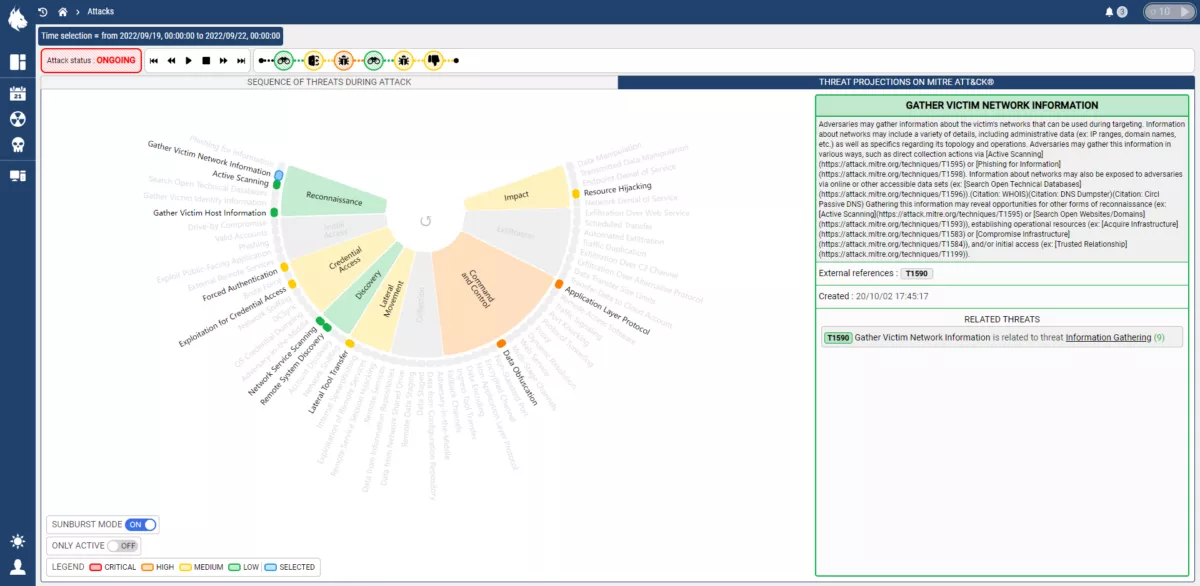
The Custocy NDR combines new AI technology with multiple sources of Threat Intelligence and projection into standards such as ENISA and the MITRE ATT&CK to track the progression of threats in real-time. An analyst can then see the course of an attack to find points of vulnerability and act BEFORE impact.
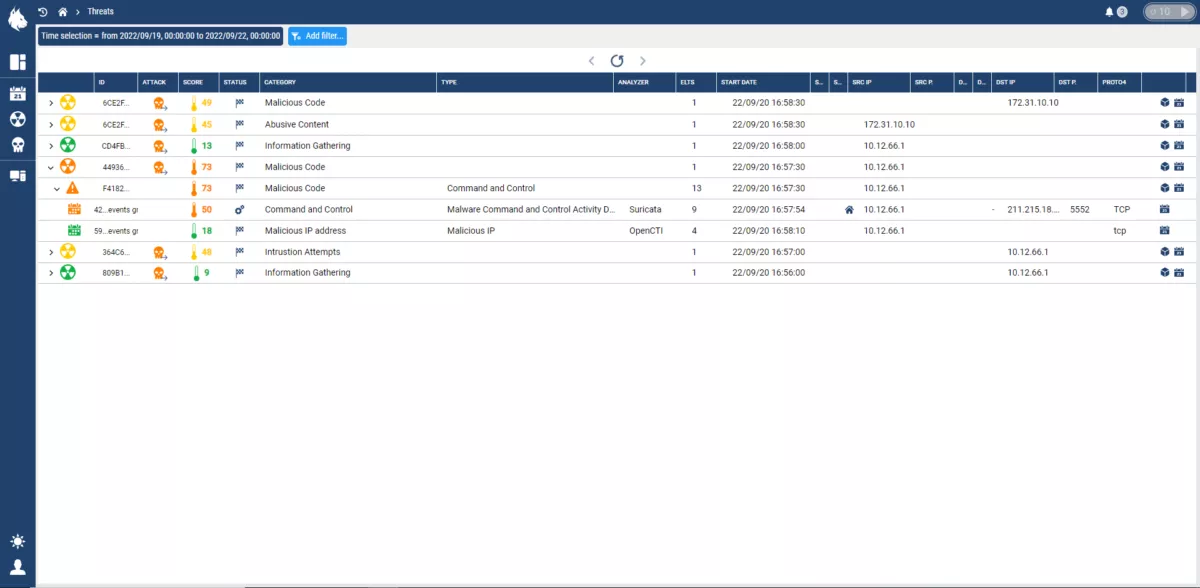
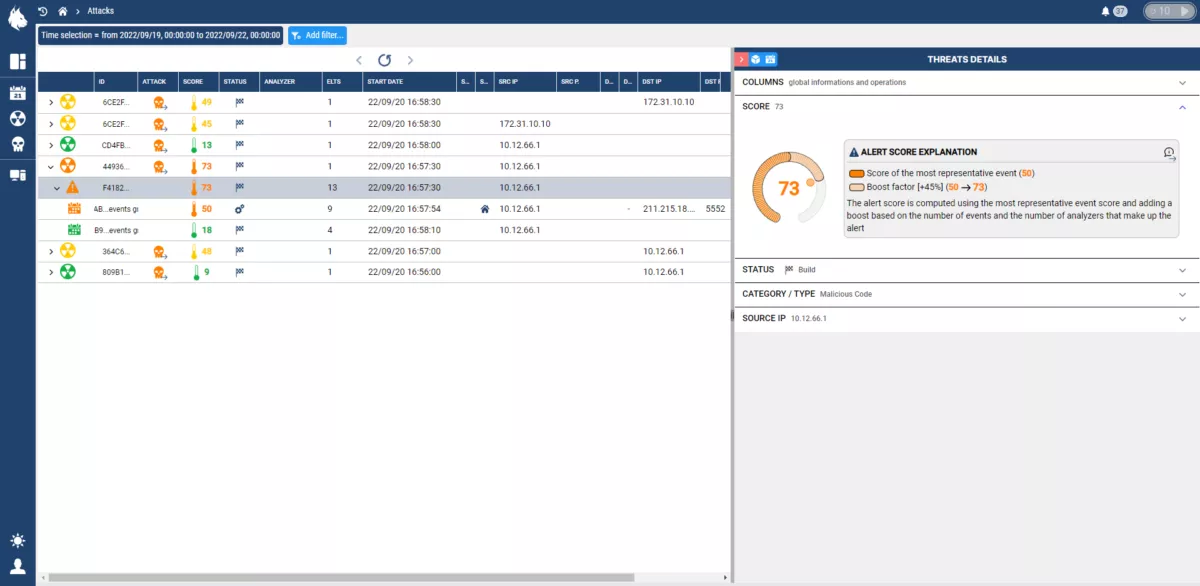
Targeted Response
With the integration of MITRE ATT&CK, an analyst will know how to respond most effectively to an ongoing threat, how to investigate complex attack campaigns, and how to guard against future attacks.
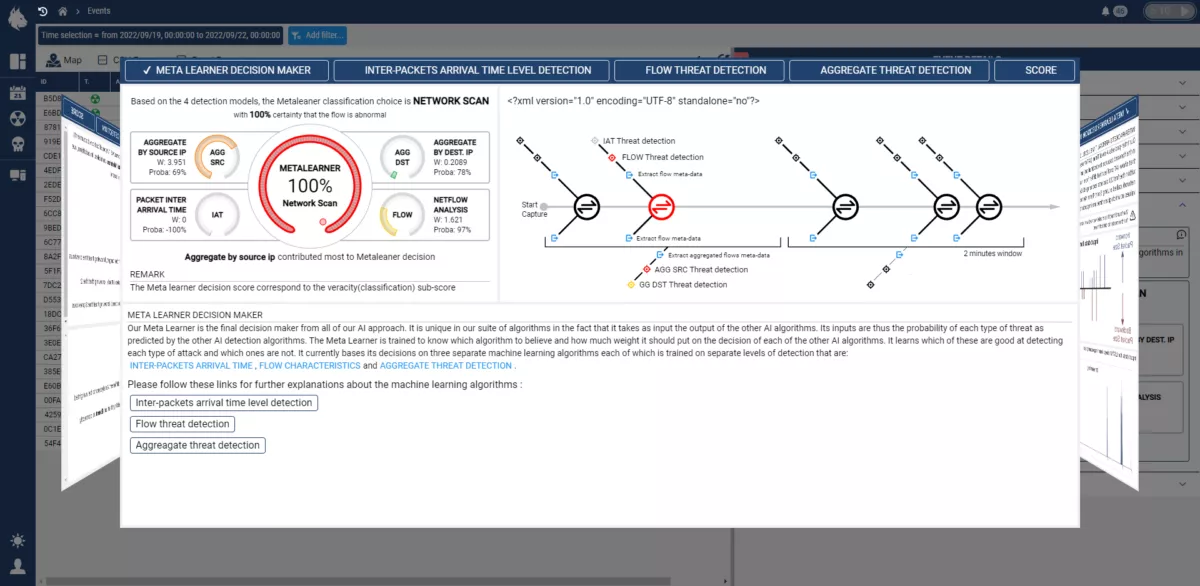
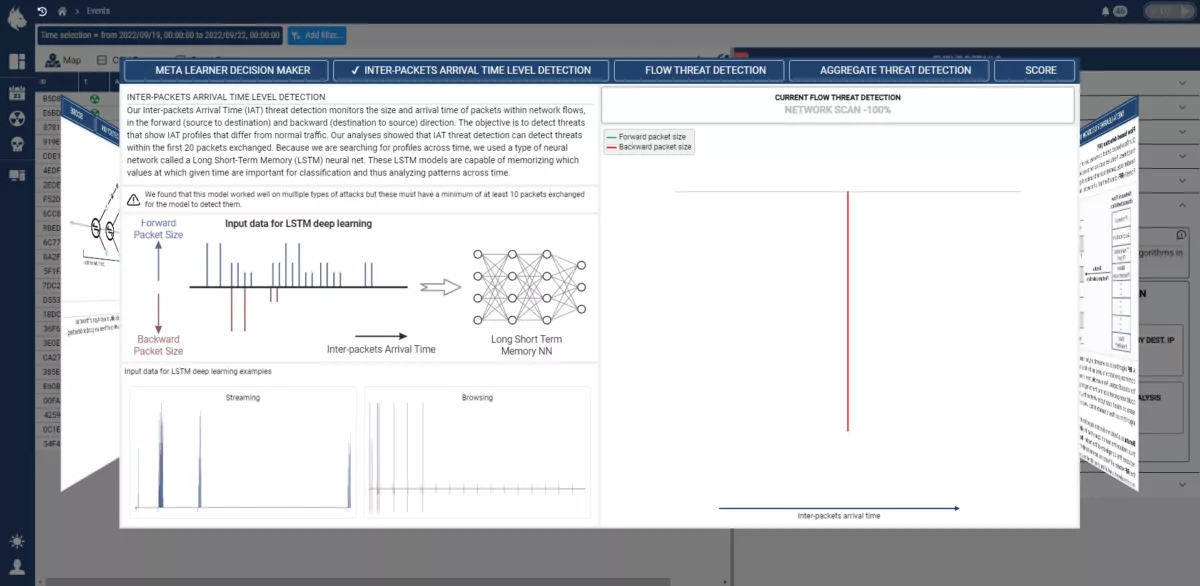
Highly explainable AI
The explainability of our AI models is an important research focus for us, no more “black boxes”. The Custocy AI explain how they make their decisions and we reveal exactly how they work, without compromising on performance.
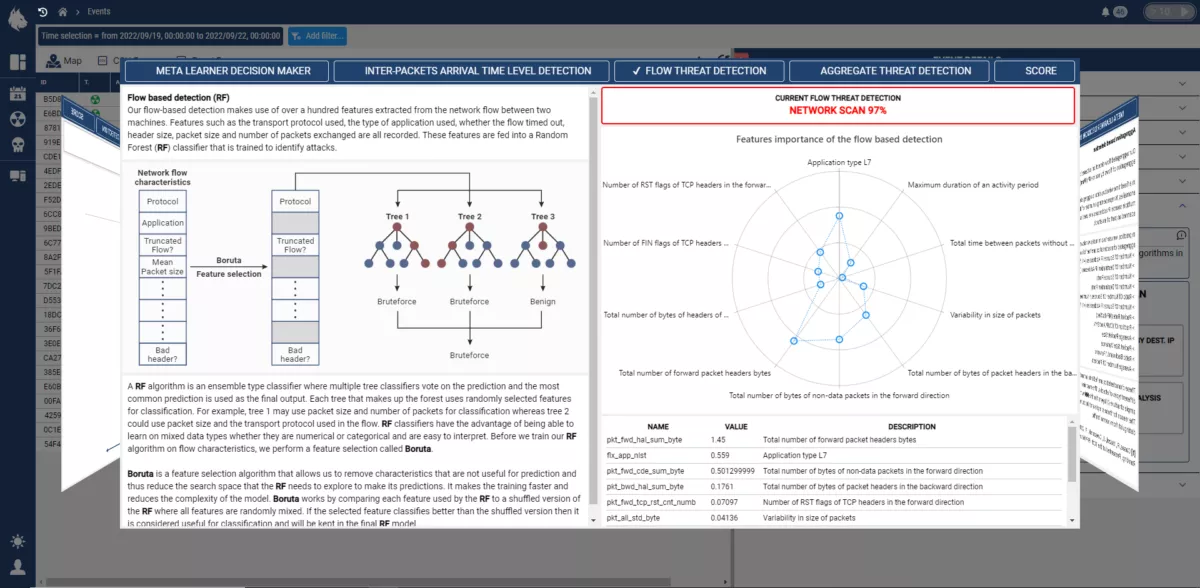
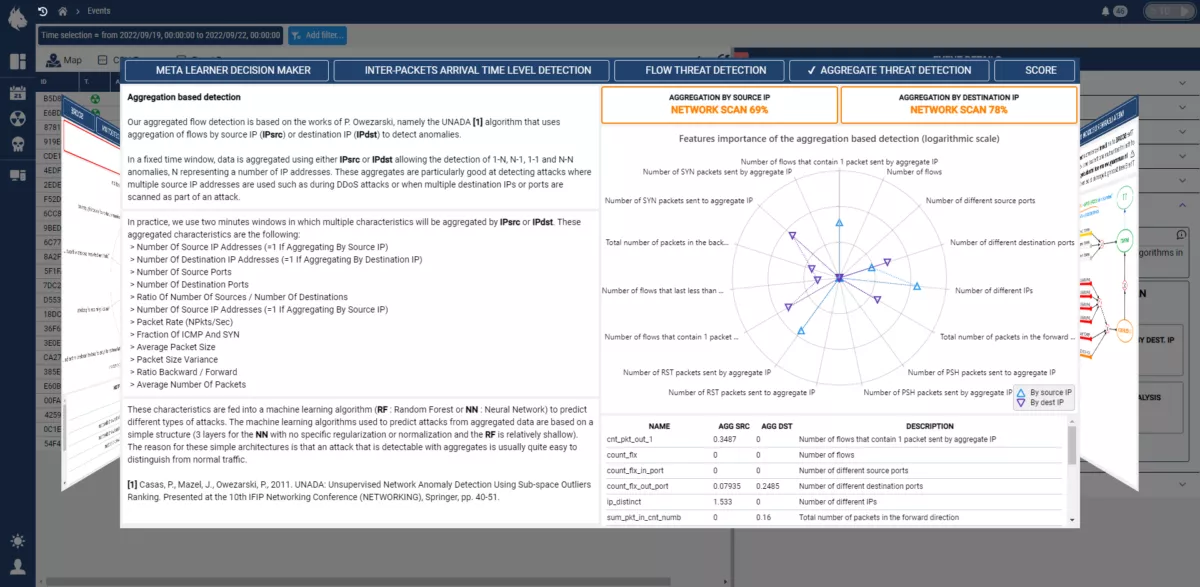
The Custocy NDR monitors your computer network to identify malicious activities at the earliest stage, enabling a rapid response.
Powered by the strength of AI, the Custocy NDR solution can analyze a large volume of network flow data to detect unusual behaviors that might go unnoticed by traditional security tools.
With Custocy, security teams are alerted in real-time and can proactively identify risks before an attack occurs.
Reduced cognitive load
Arm your security team with an advanced detection solution that makes their work easier and enhance productivity with 88 times less false positives. Your cyber analysts will no longer be overwhelmed by a barrage of alerts.
Optimised security
Make sure you reliably detect threats that other tools cannot. The Custocy Cyber Platform is a complementary security brick that can be used through its intuitive interface or integrated with the existing ecosystem (SIEM, EDR, XDR, etc.) without any prerequisites.
Increased network visibility
Stay ahead of the game by visualising and analysing malicious activity on your company's network: lateral movements, privilege escalation, command and control, detection of vulnerable assets...

Custocy at a glance
- Network monitoring based on unique collaborative AI technology
- Advanced Persistent Threat Detection
- Detection of unknown attacks (Zero-Day)
- 88 times less false positives
- Integrated response with MITRE ATT&CK
- Advanced explainability of our AI
